
Image: Microsoft. Azure Space uses the power of cloud and space technology to help businesses solve some of the world’s most challenging problems. Microsoft’s move into space shouldn’t be surprising; it’s had... Read more »

Jack Wallen walks you through the process of installing the container runtime Podman on Ubuntu Server 22.04. Image: Christian-P. Worring/Adobe Stock As you know, Kubernetes has officially deprecated Docker support, which means... Read more »

See what features you can expect from Cylance and CrowdStrike to choose the EDR solution that is ideal for your business. Image: joyfotoliakid/Adobe Stock The best endpoint detection and response tools can... Read more »

Image: Song_about_summer/Adobe Stock Containers and microservices have become the darling technology of enterprise businesses. This is especially true if your company has adopted CI/CD and DevOps solutions or is looking to become... Read more »

At its Futurestack conference, New Relic announced it expanded the integrations and tools it provides for its observability platform and added its first cybersecurity tool. The company now provides more than 470... Read more »

A clickwrap agreement, also known as a click through, shrink-wrap, or sign-in-wrap, is an online agreement in which the user signifies his or her acceptance by clicking a button or checking a... Read more »

Hypervisor security is the process of ensuring the hypervisor, the software that enables virtualization, is secure throughout its life cycle. This includes during development and in implementation. Common security practices for hypervisors... Read more »

As powerful as the cloud may be, it’s not magic. If you have a problem before you transition to the cloud, it won’t… just go away once you make the switch. Cloud... Read more »

AWS provides a set of security controls to protect its own infrastructure, but it’s important to be aware that… the security of the individual servers is the responsibility of the client —... Read more »
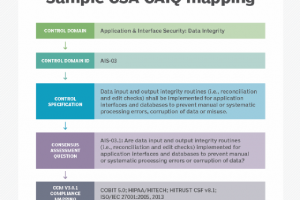
The cloud has been — and continues to be — a challenge area for many security teams. It’s a continual struggle… to validate and onboard new providers, particularly given the rapid pace... Read more »
