
A clickwrap agreement, also known as a click through, shrink-wrap, or sign-in-wrap, is an online agreement in which the user signifies his or her acceptance by clicking a button or checking a... Read more »

Hypervisor security is the process of ensuring the hypervisor, the software that enables virtualization, is secure throughout its life cycle. This includes during development and in implementation. Common security practices for hypervisors... Read more »

As powerful as the cloud may be, it’s not magic. If you have a problem before you transition to the cloud, it won’t… just go away once you make the switch. Cloud... Read more »

AWS provides a set of security controls to protect its own infrastructure, but it’s important to be aware that… the security of the individual servers is the responsibility of the client —... Read more »
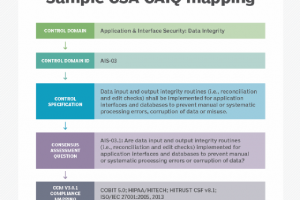
The cloud has been — and continues to be — a challenge area for many security teams. It’s a continual struggle… to validate and onboard new providers, particularly given the rapid pace... Read more »

the cloud without managing the servers themselves. When working with the cloud platform, there are two Azure service roles on which an application can be installed: web roles or worker roles. The... Read more »

Today, it’s the rare organization that hosts all its applications on premises. The emergence of cloud applications has helped companies of all shapes and sizes reduce costs, improve collaboration and ensure scalability.... Read more »

olegusk – stock.adobe.com By Whether it’s deploying cloud security services to better protect systems and data, or using cloud workloads to improve accessibility, scalability, communication and collaboration between employees and partners, the... Read more »
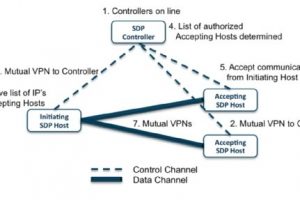
The software-defined perimeter, or SDP, is a security framework that controls access to resources based on identity. By establishing a perimeter via software versus hardware, an SDP hides an organization’s infrastructure —... Read more »
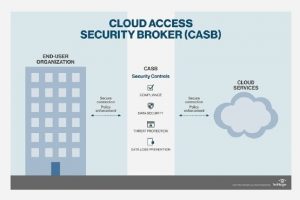
A cloud access security broker (CASB) is a software tool or service that sits between an organization’s on-premises infrastructure and a cloud provider’s infrastructure. CASBs are available as both an on-premises or... Read more »
