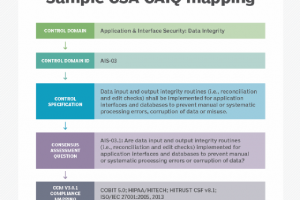
The cloud has been — and continues to be — a challenge area for many security teams. It’s a continual struggle… to validate and onboard new providers, particularly given the rapid pace... Read more »

the cloud without managing the servers themselves. When working with the cloud platform, there are two Azure service roles on which an application can be installed: web roles or worker roles. The... Read more »

Today, it’s the rare organization that hosts all its applications on premises. The emergence of cloud applications has helped companies of all shapes and sizes reduce costs, improve collaboration and ensure scalability.... Read more »

olegusk – stock.adobe.com By Whether it’s deploying cloud security services to better protect systems and data, or using cloud workloads to improve accessibility, scalability, communication and collaboration between employees and partners, the... Read more »
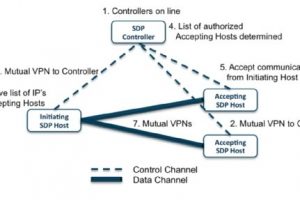
The software-defined perimeter, or SDP, is a security framework that controls access to resources based on identity. By establishing a perimeter via software versus hardware, an SDP hides an organization’s infrastructure —... Read more »
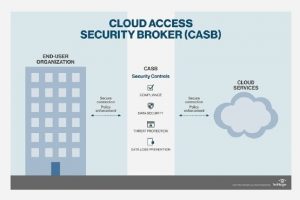
A cloud access security broker (CASB) is a software tool or service that sits between an organization’s on-premises infrastructure and a cloud provider’s infrastructure. CASBs are available as both an on-premises or... Read more »

The business and technological impacts of the COVID-19 pandemic continue to reverberate around the world. As shutdowns loomed, organizations hurriedly rolled out remote work amid steadily increasing cloud adoption trends — and... Read more »
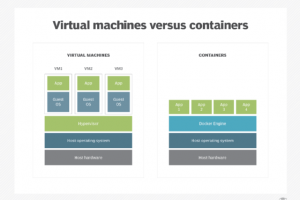
Cloud containers remain a hot topic in the IT world in general, especially in security. The world’s top technology companies, including Microsoft, Google and Facebook, all use them. For example, Google said... Read more »

What is a virtual firewall? A virtual firewall is a firewall device or service that provides network traffic filtering and monitoring for virtual machines (VMs) in a virtualized environment. Like a traditional... Read more »

More data than ever before is being put into cloud-based storage repositories. Leading cloud providers offer an array of storage options, yet databases remain the most common choice in today’s enterprises. Because... Read more »
